Optimizing NAT Gateway Usage: Transitioning to Squid Proxy
Written on
Chapter 1: Introduction to Network Management
In typical scenarios, we deploy instances within a private network of our Virtual Private Cloud (VPC) to ensure their security. However, these instances require outbound internet access for essential functions like acquiring the latest OS security updates and allowing certain applications to connect to external URLs. Commonly, we utilize cloud-native solutions such as NAT Gateway to facilitate this internet connectivity.
The diagram below illustrates a standard setup for using NAT Gateway:
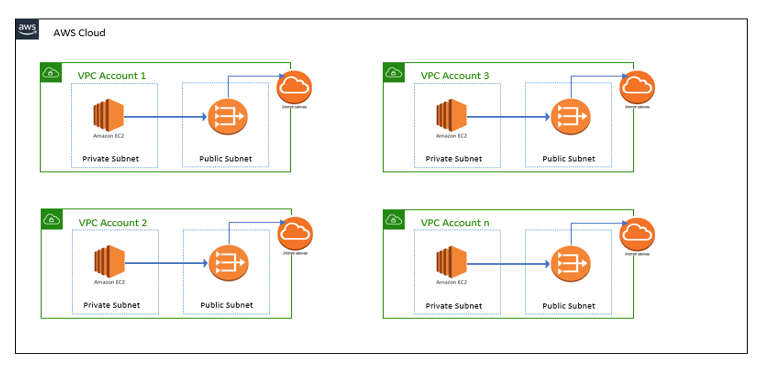
While NAT Gateways are designed to be highly available and manage most operational tasks, complexities arise when organizations operate multiple AWS accounts. Each account typically requires its own NAT Gateway, leading to several challenges.
Section 1.1: Challenges of NAT Gateway Deployment
Here are some notable drawbacks associated with using NAT Gateways:
- Cost Implications: Expenses escalate with the number of NAT Gateways required across various accounts.
- Traffic Management: There is no customizable ruleset for allowing or blocking traffic, which can include access to potentially harmful websites.
- Lack of Centralized Logging: Logs are not aggregated in one location, leading to difficulties in monitoring and control.
Subsection 1.1.1: A Centralized Proxy Solution
To mitigate these issues, a centralized proxy solution is implemented. By utilizing Squid Proxy (an open-source tool), organizations can achieve greater control over outbound connections from a single location. This setup is not only highly available and scalable but also supports multiple tenants, ultimately reducing both costs and operational efforts by minimizing the number of NAT Gateways needed.
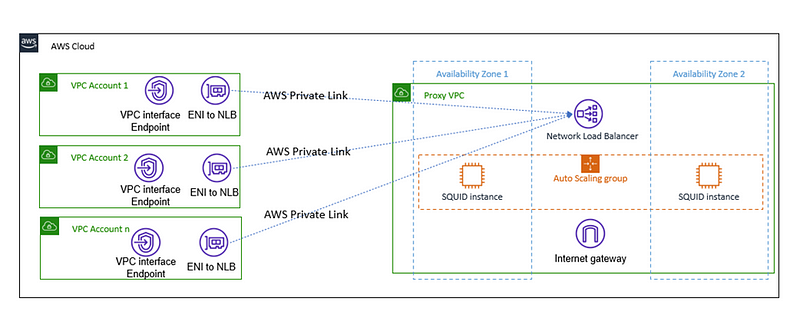
This proxy will be situated in a dedicated account with its own VPC. To ensure accessibility from each tenant's VPC, AWS PrivateLink will facilitate VPC interface endpoints. Some routing adjustments within each VPC may be necessary to connect to the VPC endpoint, which will serve as an Elastic Network Interface (ENI) tied to a specific VPC subset.
Section 1.2: Infrastructure Deployment with Terraform
For constructing this infrastructure, I opted to use Terraform. In my view, Terraform offers greater flexibility with less code compared to CloudFormation. I employed modules to enhance code readability and reusability, which also simplifies management by reducing duplication and improving testability.
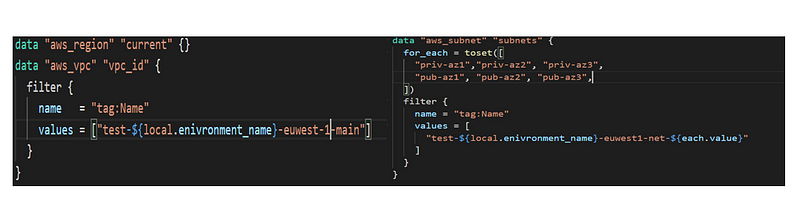
To address the challenge of integrating existing VPCs and subnets, we avoided hardcoding values in variable files. Instead, we utilized Terraform's filtering capabilities to locate the desired VPC and associated subnets based on their tag names.
Chapter 2: Environmental Separation and Configuration
This architecture allows for distinct separations between environments, providing better control over infrastructure management. By implementing this strategy, we can easily configure lightweight settings (instance types, high availability) for development and acceptance environments in contrast to the production setup.
One significant hurdle we encountered involved how to utilize the existing VPC and subnets of the account. To avoid hardcoding these values, we employed Terraform’s filtering system, enabling us to dynamically search for VPCs and their respective subnets based on tags.
Conclusion
In summary, this overall solution proves to be highly effective, allowing us to significantly reduce reliance on multiple NAT Gateways while enhancing our control over outbound connections.